As described on Data management page, the growth of global datasphere requires prompt actions to delete the expired data to mitigate the risk of losing it. The proliferation of information technology and introduction of mobile technology has forced IT managers to upgrade the technology without addressing the safe retirement of legacy data and applications. This oversight has resulted into multifold risk exposure to cases of data theft, ransomware, and huge e-discovery costs. We have observed that most of the corporations have retention schedule available but it lacks the executive sponsorship for implementation. ADT can fill that gap with confidence and quick implementation.
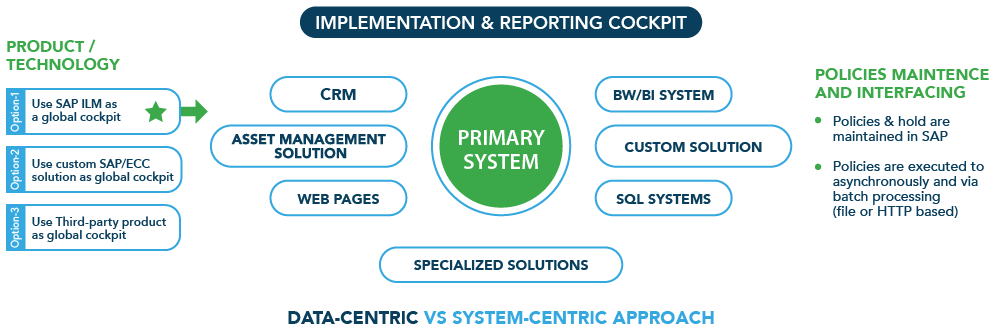
Some of the proprietary applications such as, SAP R/3/ECC/HANA, have provided a robust model to archive and retire business expired data. The archived data is available for display only through a limited APIs which limits its exposure to external interfaces and risk of theft. ADT is designed as solution extension to these existing technologies and facilitates deletion of data to secondary systems in close coordination to primary system of records. This consistency ensures a holistic deletion of data/records & documents (structure & unstructured) across various applications and legacy systems. ADT is developed on a standardized web-based interface with own secure database. ADT interfaces with proprietary, non-proprietary, and in-house systems through reuse of existing APIs/protocols and our custom APIs.
Here are some salient features of the tool:

Articulated, Precise, and Objective solutions specifically crafted for your situation.
Request now